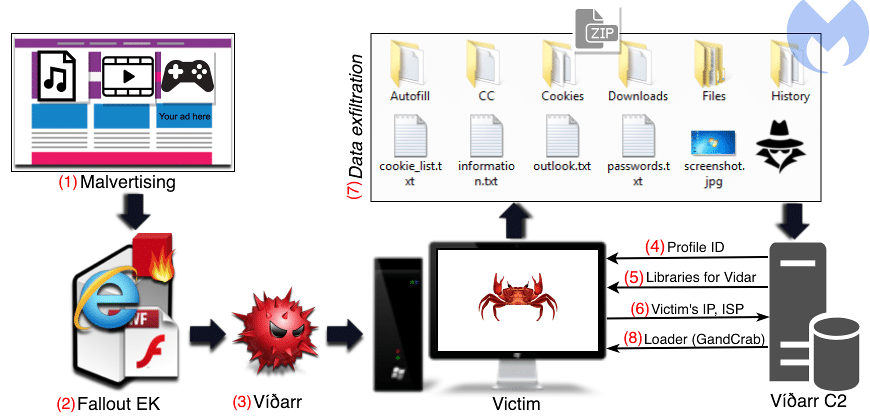
A new malware attack has been detected in the wild. This nasty combines two known pieces of malware: the Vidar data harvesting malware followed by GandCrab ransomware.
Vidar exfiltrates a wide variety of data, including passwords, documents, screenshots, stored 2FA information, and cryptocurrency wallets. and sends that to its C&C server. Next, GandCrab encrypts the infected system and displays a ransom demand. This demonic duo adds insult to injury.
Following the trails of a malvertising campaign targeting users of torrent trackers and video streaming websites, malware researchers found that Fallout Exploit Kit was used to spread a relatively new infostealer called Vidar, which doubled as a downloader for GandCrab.
Running an
Read more at
- www.theregister.co.uk: She will lock you out, livin’ la Vidar loca: Enterprising crims breed ransomware, file thief into hybrid nasty
- www.zdnet.com: Double trouble: Two-pronged cyber attack infects victims with data-stealing trojan malware and ransomware
- www.bleepingcomputer.com: GandCrab Operators Use Vidar Infostealer as a Forerunner
- www.scmagazine.com: Cybercriminals double up using Vidar and GandCrab in single attacks
Recent Comments